A hypervisor, also known as a Virtual Machine Monitor (VMM), is a software or firmware layer that enables the virtualization of physical computer hardware. Its primary function is to create and manage virtual machines (VMs) on a single physical host. These virtual machines act as independent, isolated instances, each running its own operating system and applications.
A virtual machine (VM) is a software-based emulation of a physical computer that operates within a hypervisor on a host system. It is capable of running its own operating system and applications, and multiple VMs can coexist on the same physical hardware, each isolated from the others.
Types of Hypervisors
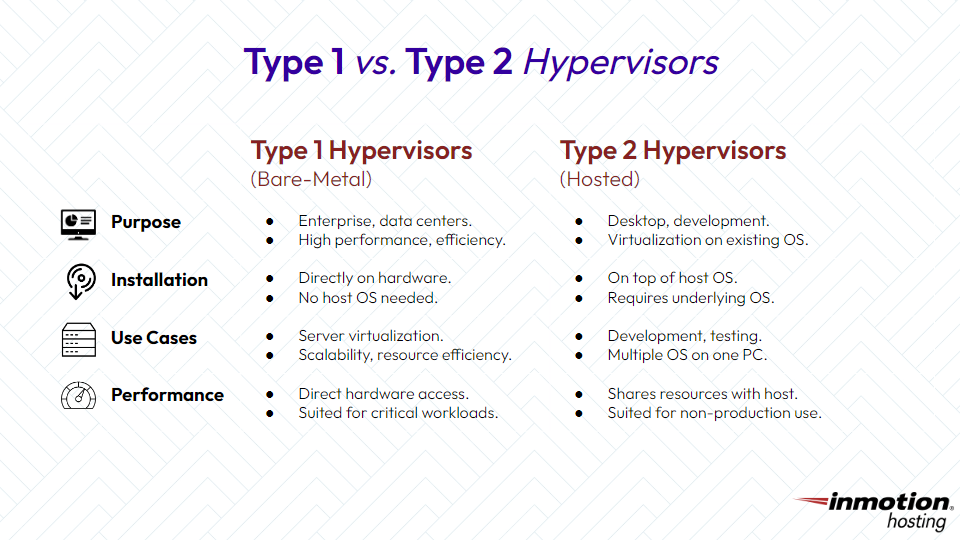
There are two main types of hypervisors:
Type 1 Hypervisor (Bare Metal Hypervisor):
This type of hypervisor, known as a Type 1 or Bare Metal Hypervisor, runs directly on the physical hardware of the host system. It does not require a host operating system and is often considered more efficient because it has direct access to hardware resources.
The term “bare metal” in the context of servers refers to a physical server that is not virtualized, meaning it runs directly on the underlying hardware without the need for a hypervisor. Bare metal servers offer advantages such as dedicated resources, high performance, and direct access to hardware. However, it’s worth noting that the specific benefits can vary depending on the use case and requirements. If the term “bare metal” is unfamiliar, learn more by reading what is a bare metal sever and reviewing the server specs on our bare metal hosting page.
Examples of Type 1 Hypervisors
VMware ESXi
VMware ESXi is a leading hypervisor in enterprise environments. Renowned for its stability and feature-rich platform, ESXi enables organizations to efficiently run multiple virtual machines on a single physical server.
Microsoft Hyper-V Server
Microsoft’s Hyper-V is a robust Type 1 hypervisor that integrates seamlessly with Windows environments. Hyper-V Server, a standalone product, delivers virtualization capabilities, empowering users to create and manage virtual machines with ease.
KVM (Kernel-based Virtual Machine)
KVM is a Linux kernel module that transforms the host operating system into a powerful hypervisor. It operates in conjunction with other components to provide a comprehensive virtualization solution, combining performance with the flexibility of Linux environments.
Additional Type 1 Hypervisors include: Xen, Oracle VM Server, Proxmox Virtual Environment, and Nutanix AHV.
Type 2 Hypervisor (Hosted Hypervisor):
A Type 2 hypervisor runs on top of a host operating system. It is installed like any other software application and creates virtual machines within the host operating system. While generally easier to set up, Type 2 hypervisors introduce additional overhead as they rely on the host operating system for resource management.
Examples of Type 2 Hypervisors
Oracle VirtualBox
Oracle VirtualBox is a widely used open-source Type 2 hypervisor that supports a variety of guest operating systems. Known for its user-friendly interface, VirtualBox is a popular choice for developers and enthusiasts exploring virtualization on their desktops.
VMware Workstation
VMware Workstation is a powerful Type 2 hypervisor that caters to professionals and developers. It allows users to create and manage virtual machines on their desktops, providing a flexible environment for testing and development purposes.
Parallels Desktop
Designed specifically for macOS, Parallels Desktop is a Type 2 hypervisor that enables users to run Windows and other operating systems alongside macOS. It’s a favored choice for individuals requiring seamless integration between different platforms.
Additional Type 2 Hypervisors include: Microsoft Hyper-V (Windows Desktop Version), VMware Player, Docker Desktop, and Virtual PC.
What does a Hypervisor do?
Resource Allocation
Hypervisors play a crucial role in resource allocation within a virtualized environment. Resource allocation refers to the distribution and management of physical hardware resources such as CPU, memory (RAM), storage, and network bandwidth among virtual machines (VMs) running on a single physical host.
CPU Allocation
The hypervisor oversees the allocation of CPU resources among virtual machines. It ensures that each VM receives a fair share of processing power, preventing one VM from monopolizing the CPU and impeding the performance of others. Additionally, some hypervisors support features like CPU affinity, allowing VMs to be assigned to specific CPU cores for optimized performance.
Memory Allocation
Memory allocation involves distributing the available RAM among virtual machines. Hypervisors manage memory usage dynamically, adjusting allocations based on the demands of each VM. They employ techniques such as ballooning (adjusting VM memory usage by inflating or deflating the balloon driver within the VM) and memory overcommitment to optimize the use of available memory resources.
Storage Allocation
Hypervisors manage the allocation of storage resources by creating virtual disks for each VM. These virtual disks are mapped to physical storage devices on the host. Advanced storage features like thin provisioning allow more efficient use of storage space by allocating physical space only as needed.
Virtual Machine Management
One of the fundamental functions of a hypervisor is the seamless management of virtual machines (VMs), offering administrators the ability to create, delete, and oversee the dynamic lifecycle of these virtualized entities. This capability plays a pivotal role in the flexibility and adaptability of virtualized environments.
Creation and Configuration
The hypervisor streamlines the process of creating new virtual machines, providing administrators with intuitive interfaces or command-line tools to specify configurations such as CPU allocation, memory size, and storage capacity. This allows for the rapid deployment of virtualized instances tailored to specific workloads or applications. Moreover, the hypervisor enables the customization of individual VMs, including the installation of guest operating systems and the configuration of network settings, ensuring that each virtual machine aligns with the distinct requirements of its intended use.
Operating System Diversity:
A key advantage facilitated by the hypervisor is its support for a diverse array of operating systems running concurrently on the same physical hardware. This feature is particularly valuable in mixed IT environments where different operating systems are necessary for varied applications or specific business needs. The hypervisor abstracts the underlying hardware, allowing VMs to run operating systems independent of the host system, thereby fostering an environment where Windows, Linux, or other operating systems coexist harmoniously.
Performance Optimization
Hypervisors aim to optimize resource utilization, ensuring that virtual machines run efficiently and that the overall system performs well.
Hypervisors continuously monitor the resource usage of each VM. In response to changing workloads, they dynamically adjust resource allocations to prevent performance bottlenecks. For example, if a VM requires additional CPU or memory during peak usage, the hypervisor can allocate more resources temporarily.
Hypervisors are fundamental components in virtualization technology, enabling the consolidation of multiple virtualized environments on a single physical server. This brings benefits such as improved resource utilization, easier management, and greater flexibility in deploying and scaling applications.
Are Hypervisors Secure?
The security of hypervisors is critical. If you’re questioning the security of hypervisors, it’s important to recognize that any identified vulnerability at this level has the potential to compromise the integrity and security of all virtual machines hosted within.
To address this, hypervisors typically undergo rigorous security measures, including regular updates and configurations that enhance resilience against potential threats. Organizations and users leveraging virtualization technology must remain vigilant, adopting best practices to fortify the security of hypervisors and the virtual environments they manage.
When evaluating hypervisor security, it’s also important to consider the broader context of bare metal server security. The foundational security of the underlying hardware, provided by bare metal servers, is interconnected with the overall security of virtualized environments.
