
In an era dominated by digitization and interconnectedness, the importance of cybersecurity cannot be overstated. Organizations of all sizes are under constant threat from cyberattacks, data breaches, and other security vulnerabilities. As a response to these challenges, the concept of bare metal servers has gained prominence as a way to bolster security measures. In this article, we take a closer look at baremetal servers and explore why they are considered more secure compared to their virtualized counterparts.
Understanding Bare Metal Servers
Before we jump into the security advantages, it’s essential to understand what exactly bare metal servers are. Unlike virtualized or cloud servers, which operate within a hypervisor layer that abstracts hardware resources, bare metal servers are physical machines without any virtualization layer. Each bare metal server is a standalone entity, providing dedicated resources to a single tenant. This fundamental difference in architecture plays a pivotal role in enhancing security.
Security Advantages of Bare Metal Servers
1. Isolation / Defense in Depth
Defense in depth is a cybersecurity strategy that involves deploying multiple layers of security mechanisms and measures to protect a system or network. The concept recognizes that no single security measure is foolproof, and by implementing a variety of safeguards at different levels, organizations can create a more resilient defense against a wide range of security threats.
Isolation within bare metal server environments is a type of defense in depth. By segmenting different workloads onto separate physical servers, a breach or compromise in one instance is less likely to cascade to others. In the event of an attack, the isolation prevents the threat from spreading across the bare metal infrastructure, minimizing the potential damage and reducing the attacker’s ability to escalate privileges.
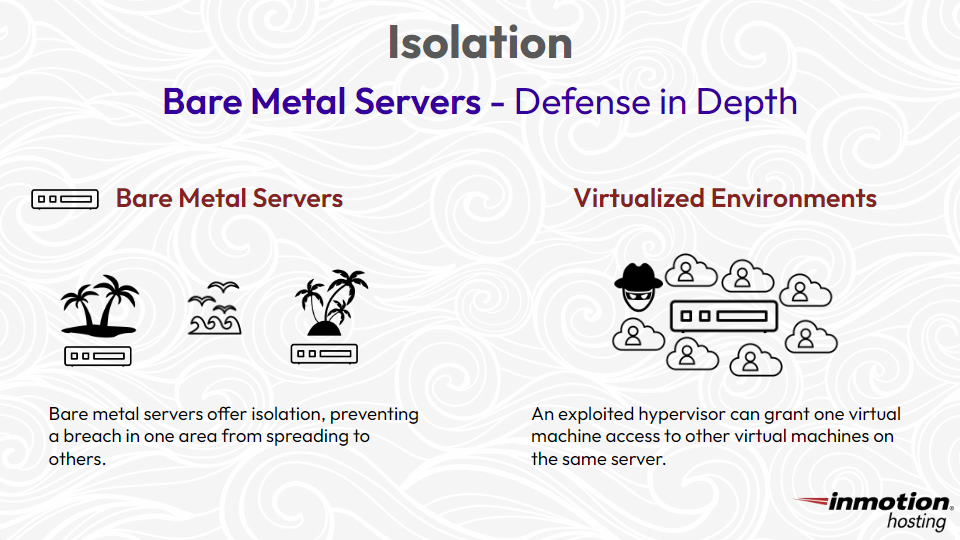
Think of bare metal servers as individual islands. Each island (server) is separate from the others, running on its dedicated hardware. This means that if something goes wrong on one island, it doesn’t affect the others—like having your own space in a vast sea. Bare metal servers give administrators direct control over the digital ‘island,’ allowing them to set up customized security measures.
2. Reduced Attack Surface
The attack surface of a system refers to the potential points of entry for malicious actors. In virtualized environments, the hypervisor layer introduces an additional layer of complexity, potentially creating new attack vectors.
Bare metal servers, devoid of hypervisors, have a significantly smaller attack surface. The absence of this layer eliminates the vulnerabilities associated with hypervisor technologies, reducing the potential for attacks that exploit hypervisor weaknesses.
This Wired article discusses the emerging cyber threat known as “hyperjacking,” a technique where attackers exploit vulnerabilities in virtual machine (VM) platforms like VMware to gain unauthorized access to data centers. The article highlights a report by cybersecurity firm Mandiant, which describes how threat actors target VM platforms to move laterally within networks, potentially compromising sensitive data and critical infrastructure. Hyperjacking involves manipulating the VM hypervisor layer to achieve unauthorized access, posing risks to organizations using virtualized environments. The report emphasizes the need for vigilant security measures, regular updates, and monitoring to prevent and mitigate hyperjacking attacks.
Hypervisor exploit examples
Below, we’ll review a few hypervisor attacks and vulnerabilities over the years
ESXiArgs
ESXi is a hypervisor that VMware sells to cloud hosting providers. In 2021, VMware patched the vulnerability CVE-2021-21974, which had a severity rating of 8.8 out of 10. Attackers were exploiting this vulnerability to install ransomware on virtual machines.
In their investigation, CERT (Computer Emergency Response Teams) reported that over 3,200 servers were infected.
OVH, a hosting provider in France, reported that they were unable to patch the vulnerability for customers with unmanaged servers. The most they could do was block port 427 (the port used for access) and then attempt to notify all customers whom they believed could be targeted.
PS5 Hypervisor exploit
In 2023, a user claimed to have hacked the PS5 hypervisor using an exploit via a disc-based PS4 savegame exploit. This exploit gives someone access to PS5 decryption keys, which would allow them to decrypt firmware files and game files.
Venom Hypervisor Vulnerability
In 2015, Crowdstrike brought to light a critical vulnerability named “Venom” (CVE-2015-3456) affecting hypervisors like KVM, QEMU, and Xen. This flaw resided in the floppy disk driver, enabling a guest OS to breach the hypervisor and access the host OS.
The discovery fell into the category of grave hypervisor vulnerabilities, as it permitted attackers to compromise not only other guest systems but also attempt lateral movements to infiltrate host systems.
Mitigating these types of risks isn’t so straightforward at the guest level – typically within user control – as the fix requires intervention at the host level. This echoes past instances where hypervisor vulnerabilities demanded host-level attention, emphasizing the critical need for comprehensive security measures at the infrastructure layer.
3. Enhanced Control and Customization
A bare metal server offers more customizable security configurations compared to a virtual machine (VM) primarily due to its direct access to dedicated hardware resources and the absence of a hypervisor layer.
In a bare metal server, you have exclusive access to the entire physical hardware stack, including CPU, memory, storage, and network interfaces. This allows for granular control over security settings at the hardware level, such as hardware firewalls and hardware-based encryption mechanisms.
A hardware firewall bolsters the security of a bare metal server compared to a virtual private server (VPS) by providing dedicated protection and direct control over network traffic at the physical level. With isolation from other tenants, customizable security policies, deep traffic inspection, and protection against DDoS attacks, the hardware firewall enhances defense mechanisms. It enables network segmentation, efficient monitoring, and offloading server load, contributing to robust security. In contrast to VPS environments, which might rely on software-based firewalls, the hardware firewall’s capacity for granular control and tailored protection makes it a powerful safeguard for bare metal servers against a variety of cyber threats.
Use Cases and Industries
Bare metal servers find relevance in a multitude of industries and scenarios where security is paramount:
Finance and Banking: In an industry where data privacy and regulatory compliance are of utmost importance, bare metal servers provide the level of security necessary to protect sensitive financial information.
Healthcare and Medical Research: The healthcare sector deals with highly confidential patient data and medical research findings. Bare metal servers ensure that this critical data remains isolated and secure.
Government and Military Sectors: Government agencies and military organizations handle classified information that demands the highest level of security. Bare metal servers offer the necessary level of control and isolation to safeguard national security interests.
Data-Intensive Research Projects: Research projects involving proprietary algorithms, experimental data, or confidential research findings can benefit from the enhanced security of bare metal servers.
Challenges and Considerations
While bare metal servers offer compelling security advantages, it’s important to acknowledge certain challenges and considerations:
Higher Upfront Costs: Implementing bare metal servers typically incurs higher initial costs compared to virtualized solutions. Organizations need to weigh the cost-benefit ratio of enhanced security against the investment required.
Limited Scalability: Bare metal servers might not scale as easily as cloud environments. If rapid scalability is a critical requirement, organizations should carefully assess their needs.
Resource Management Complexities: The increased control over hardware and software can lead to more complex resource management. Organizations must ensure that they have the expertise to manage and optimize these resources effectively.
Conclusion
In an increasingly interconnected world, cybersecurity remains a top priority. Bare metal servers present a compelling solution to address the ever-evolving threat landscape. With their isolation, reduced attack surface, and emphasis on physical security, bare metal servers offer a level of security that is particularly well-suited for industries and scenarios where data protection is paramount. While bare metal servers have both advantages and disadvantages, organizations that prioritize security should consider the adoption of bare metal servers as a strategic move to fortify their digital defenses in an age of heightened cyber threats.
Experience unrestricted processing power on state-of-the-art hardware and your preferred operating system with Bare Metal Hosting!
Ubuntu, Debian, OpenSUSE, or Load your own OS Unmanaged Hosting
Perfect for SysAdmins
Dedicated Resources
Bare Metal Servers
